XTECHNOLOGY NETWORK CORPORATION. 2010 (Ltd.)
xtechnologies@gmx.com
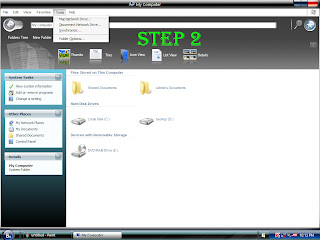
Go to your home desktop. ( Administrator )
Go to Menu bar, choose "Tools" & click at Folder Options.
On the Folder Option Box, Click at View.
To unhide any folder and any file in your system,
makesure You choose "Show Hidden file and folder".
Then if you want to hide it back,
choose "Do not show hidden file and folder".
Then just click Apply and Ok.
Quick Simple Easy.
Add by Xtechnology Admin.
12:09 AM Sunday 3rd Oct 2010.